Blog Posts
- Home /
- Blog Posts
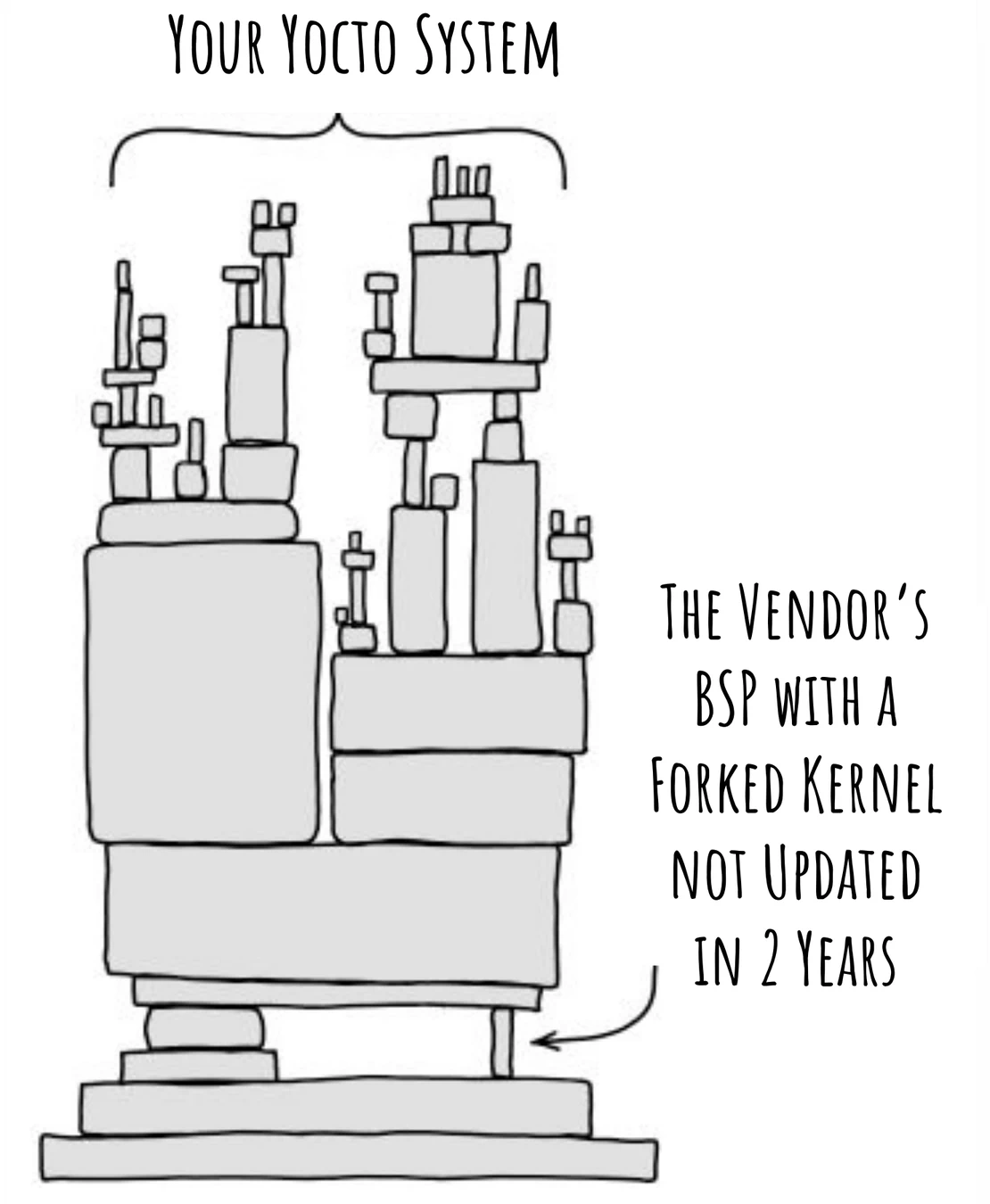
Yocto Vendor BSPs - The good, the bad, the ugly
- Anna-Lena Marx
- November 6, 2025
- Embedded , Conferences
Vendor Board Support Packages (BSPs) promise a quick start, but we all know the reality: a tangled mess of demo apps, weird custom tools, and an old, unmaintained kernel. This is a nightmare for products that need to live longer than a demo on the developer’s desk.
In this talk, we get our hands dirty. Forget the polished slides; we’re going to take a live, no-holds-barred look at some real-world vendor BSPs to see the common pain points firsthand. From there, we’ll discuss what we actually need from a BSP for a production device and explore the tipping point where setting up your own clean foundation becomes the smarter choice for building products that are meant to last.
Read Post
Building Trust - Use Cases and Implementation of TPM 2.0 in Embedded Linux Systems
- Anna-Lena Marx
- May 16, 2025
- Embedded , Conferences
Artwork by: Sparkelle (Yan) — Licensed under Creative Commons BY-SA 4.0
As embedded systems become increasingly interconnected, the demand for robust platform security and integrity has surged. Trusted Platform Modules (TPM), currently in version 2.0, are becoming increasingly beneficial for enhancing security in embedded systems. TPMs provide hardware-backed mechanisms for critical functions such as random number generation, cryptographic key generation, key binding and data sealing.
This presentation will explore the capabilities of TPM 2.0, focusing on several practical use cases, including:
Read Post